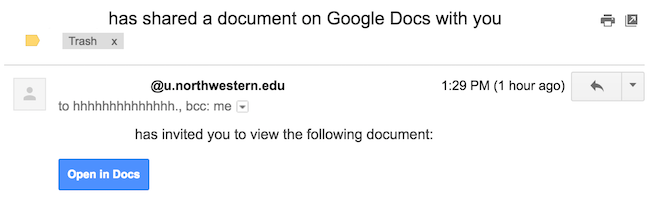
Google Docs has fallen prey to yet another phishing scam. Around 1:30 p.m., people across all Gmail domains received emails sharing Google Docs with them, from friends, fellow students or other harmless contacts.
But these emails are not harmless. They are part of a widespread phishing scam that takes advantage of Google Docs. Those who open the email are redirected to a login page that allows hackers to gather user information and access their online accounts. Why they might want this information? To spread further hacks, or to gather information to all user accounts (i.e. Amazon, Facebook or Apple).
This same scam occurred in March of 2014, and a similar scam, which shared an audio file instead of a document, happened in January this year.
Why do these scams keep happening? For one, the hack is almost impossible to recognize. The scam login page uses a google.com URL, so all seems well, and once you enter your information, it even directs you to a real Google Doc — one that has been made public on a Google account, set up by the hackers. Meanwhile, your Google credentials are sent to a compromised server, and the hackers are given access to all your Google information.
Northwestern uses a separate domain within the Google system; this domain is currently being hacked. However, so are others across the country, including other school districts and Buzzfeed, who even felt it pertinent enough to warn about the mysterious shared doc.
If you think you have been hacked, know you are not alone. The best thing you can do is change your account password, and delete any emails you think may be hacks. You can also change your privacy and security settings, to make sure you delete the fake account from having access to your docs. And though we’re already traumatized by Caesar’s multi-factor authentication, you can set up the same dual login process between your Google account and your phone.
Though Google has not yet commented on the attack, the emails have stopped, which means the phishing has probably been put to an end.